.java Files Virus (Dharma Ransomware) – Remove and Restore Files
This article aims to help you remove the newly discovered variant of Dharma ransomware virus and show you how you can try and restore as many files, encrypted with .java extension as possible without having to pay ransom to the cyber-criminals behind it.
New variant of Dharma ransomware virus has been detected by malware researchers. The virus uses the .java extension and a unique identification number (for example id-3293991412412.java) which it adds to the files that are encrypted by it. The ransomware also drops a ransom note, which further aims to extort the victims of the virus into paying a hefty ransom fee in order to get access to their encrypted files and make them openable again. In the event that your computer has been infected with this variant of Dharma ransomware, we recommend that you read this article in order to learn how to remove the .java files virus from your computer and try to restore encrypted files.
| Name | .java Dharma Virus |
| Type | Ransomware, Cryptovirus |
| Short Description | New variant of Dharma/CrySiS ransomware family. Uses encryption to make important files on infected PC’s no longer openable and then extorts the victim for payment to get the files back. |
| Symptoms | Encrypts documents, images, videos and other important files and adds the .java file extension after their filename and original extension. |
| Distribution Method | Spam Emails, Email Attachments, Executable files |
| Detection Tool | See If Your System Has Been Affected by .java Dharma Virus
|
| User Experience | Join Our Forum to Discuss .java Dharma Virus. |
| Data Recovery Tool | Windows Data Recovery by Stellar Phoenix Notice! This product scans your drive sectors to recover lost files and it may not recover 100% of the encrypted files, but only few of them, depending on the situation and whether or not you have reformatted your drive. |

Update January 2018 – .java Uses New E-mail and Has Other Changes
The infection file for the new version has been uploaded to VirusTotal.com with the following parameters:


.java Files Virus – How Does It Infect
- Invoices.
- Banking statements.
- Receipts of purchases the user does not recall in making.
- Other important documents.
In addition to via e-mail, the malicious files of .java file extension virus may also be concealed as a legitimate setups of programs, key generators, game fixes, patches, cracks and other software license activators, so users should be careful which websites they download software from and always check the downloaded files on demand. If you do not have any protection software, recommendations are to use an anti-malware program which can automatically scan the files after you have downloaded them and detected if they are malicious or clean.

Dharma .java Files Virus – Malicious Activity
- Touch system files.
- Create mutexes.
- Interact with the Windows Registry Editor.
- Delete system backups and shadow volume copies.
- Change wallpaper and drop it’s ransom note so that it can be seen.
- %AppData%
- %Roaming%
- %Local%
- %LocalLow%
- %Temp%
→ HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\
Since
those keys are responsible for running programs alongside Windows Boot,
the virus may also begin to delete the shadow volume copies on the
infected machine which makes restoring your files via backup impossible.
To do this, the .java file virus may use the following commands in
Windows Command Prompt by running a script as an administrator that
executes them in quiet mode.HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\
→ bcdedit /set bootstatuspolicy ignoreallfailures
bcdedit /set recoveryenabled No
bcdedit /set {default} bootstatuspolicy ignoreallfailures
bcdedit /set {default} recoveryenabled No
vssadmin delete shadows /for={volume} /oldest /all /shadow={ID of the Shadow} /quiet
After doing so, the latest variant of Dharma is ready to encrypt your important files.bcdedit /set recoveryenabled No
bcdedit /set {default} bootstatuspolicy ignoreallfailures
bcdedit /set {default} recoveryenabled No
vssadmin delete shadows /for={volume} /oldest /all /shadow={ID of the Shadow} /quiet

Dharma .java Ransomware – Encryption Process
“PNG .PSD .PSPIMAGE .TGA .THM .TIF .TIFF .YUV .AI .EPS .PS .SVG .INDD .PCT .PDF .XLR .XLS .XLSX .ACCDB .DB .DBF .MDB .PDB .SQL .APK .APP .BAT .CGI .COM .EXE .GADGET .JAR .PIF .WSF .DEM .GAM .NES .ROM .SAV CAD Files .DWG .DXF GIS Files .GPX .KML .KMZ .ASP .ASPX .CER .CFM .CSR .CSS .HTM .HTML .JS .JSP .PHP .RSS .XHTML. DOC .DOCX .LOG .MSG .ODT .PAGES .RTF .TEX .TXT .WPD .WPS .CSV .DAT .GED .KEY .KEYCHAIN .PPS .PPT .PPTX ..INI .PRF Encoded Files .HQX .MIM .UUE .7Z .CBR .DEB .GZ .PKG .RAR .RPM .SITX .TAR.GZ .ZIP .ZIPX .BIN .CUE .DMG .ISO .MDF .TOAST .VCD SDF .TAR .TAX2014 .TAX2015 .VCF .XML Audio Files .AIF .IFF .M3U .M4A .MID .MP3 .MPA .WAV .WMA Video Files .3G2 .3GP .ASF .AVI .FLV .M4V .MOV .MP4 .MPG .RM .SRT .SWF .VOB .WMV 3D .3DM .3DS .MAX .OBJ R.BMP .DDS .GIF .JPG ..CRX .PLUGIN .FNT .FON .OTF .TTF .CAB .CPL .CUR .DESKTHEMEPACK .DLL .DMP .DRV .ICNS .ICO .LNK .SYS .CFG”After the files have been encrypted, they can no longer be opened and their file icon is replaced with a blank one, similar to corrupted files. This variant of Dharma ransowmare does not cheat on it’s style and adds a new file extension .java, alongside which there is a unique identification number of the infected PC and an e-mail to contact the cyber-criminals for ransom payoff. So far, we have detected the following two iterations of encrypted files by the .java Dharma virus:

Remove Dharma Ransomware and Restore .java Encrypted Files
You can try to restore files encrypted by this iteration of Dharma ransomware with the alternative methods for file recovery located below in step “2. Restore files encrypted by .java Dharma virus”. However, keep in mind that there is no guarantee that these alternative methods will work.
Manually delete .java Dharma Virus from your computer
Note! Substantial notification about the .java Dharma Virus threat: Manual removal of .java Dharma Virus
requires interference with system files and registries. Thus, it can
cause damage to your PC. Even if your computer skills are not at a
professional level, don’t worry. You can do the removal yourself just in
5 minutes, using a malware removal tool.
1. Boot Your PC In Safe Mode to isolate and remove .java Dharma Virus files and objects
Boot Your PC Into Safe Mode
 1. For Windows 7,XP and Vista.
1. For Windows 7,XP and Vista. 2. For Windows 8, 8.1 and 10.
2. For Windows 8, 8.1 and 10. Fix registry entries created by .java Dharma Virus on your PC.
Fix registry entries created by .java Dharma Virus on your PC.1. Remove all CDs and DVDs, and then Restart your PC from the “Start” menu.
2.
Select one of the two options provided below:
– For PCs with a single operating system: Press “F8” repeatedly after the first boot screen shows up during the restart of your computer. In case the Windows logo appears on the screen, you have to repeat the same task again.

– For PCs with multiple operating systems: Тhe arrow keys will help you select the operating system you prefer to start in Safe Mode. Press “F8” just as described for a single operating system.
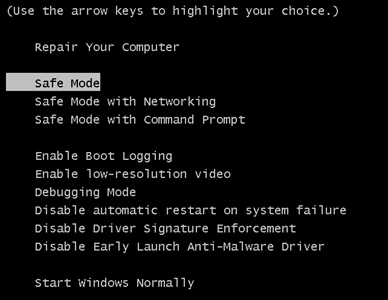
3. As the “Advanced Boot Options” screen appears, select the Safe Mode option you want using the arrow keys. As you make your selection, press “Enter“.
4. Log on to your computer using your administrator account
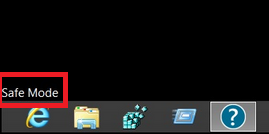
While your computer is in Safe Mode, the words “Safe Mode” will appear in all four corners of your screen.
Find malicious files created by .java Dharma Virus
 1. For Windows 8, 8.1 and 10.
1. For Windows 8, 8.1 and 10. 2. For Windows 7,XP and Vista.
2. For Windows 7,XP and Vista.For Newer Windows Operating Systems
Step 1:
On your keyboard press + R and write explorer.exe in the Run text box and then click on the Ok button.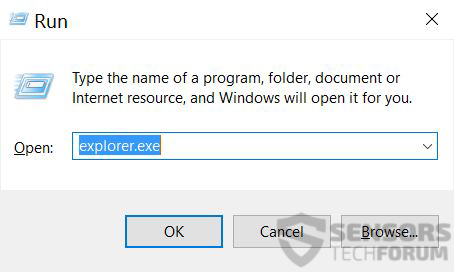
Step 2:
Click on your PC from the quick access bar. This is usually an icon with a monitor and its name is either “My Computer”, “My PC” or “This PC” or whatever you have named it.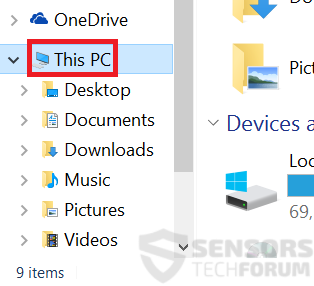
Step 3:
Navigate to the search box in the top-right of your PC’s screen and type “fileextension:” and after which type the file extension. If you are looking for malicious executables, an example may be “fileextension:exe”. After doing that, leave a space and type the file name you believe the malware has created. Here is how it may appear if your file has been found: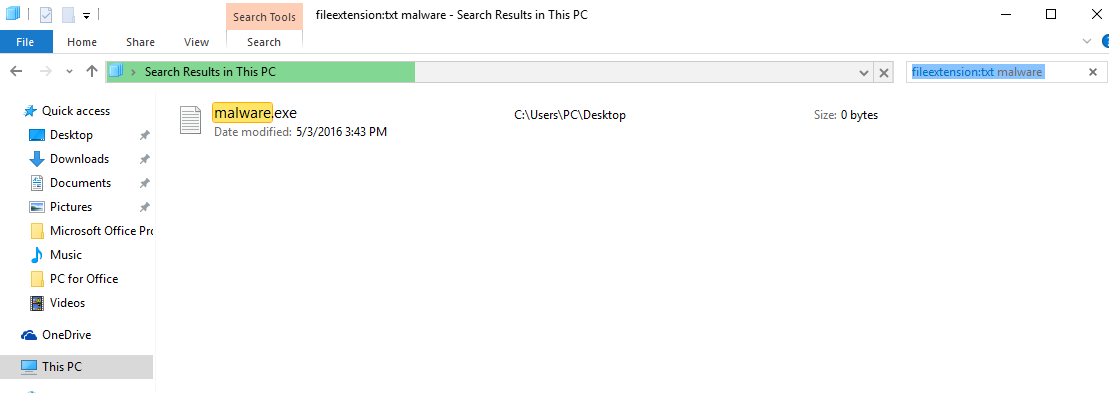
N.B. We recommend to wait for the green loading bar in the navination box to fill up in case the PC is looking for the file and hasn’t found it yet.
Automatically remove .java Dharma Virus by downloading an advanced anti-malware program
Remove .java Dharma Virus with SpyHunter Anti-Malware Tool
 1. Install SpyHunter to scan for and remove .java Dharma Virus.
1. Install SpyHunter to scan for and remove .java Dharma Virus. 2. Scan with SpyHunter to Detect and Remove .java Dharma Virus.
2. Scan with SpyHunter to Detect and Remove .java Dharma Virus.
Step 1:Click on the “Download” button to proceed to SpyHunter’s download page.
It is highly recommended to run a scan before purchasing the full version of the software to make sure that the current version of the malware can be detected by SpyHunter.
Step 2: Guide yourself by the download instructions provided for each browser.
Step 3: After you have installed SpyHunter, wait for it to automatically update.

It is highly recommended to run a scan before purchasing the full version of the software to make sure that the current version of the malware can be detected by SpyHunter.
Step 2: Guide yourself by the download instructions provided for each browser.
Step 3: After you have installed SpyHunter, wait for it to automatically update.

Restore Files Encrypted by .java Dharma Virus
Ransomware infections like .java Dharma Virus aim to encrypt your files using an encryption algorithm which may be very difficult to directly decrypt. This is why we have suggested several alternative methods that may help you go around direct decryption and try to restore your files. Bear in mind that they may not be 100% effective but they may help you little or a lot in some situations.Method 1: Scanning your drive’s sectors by using Data Recovery software.
Another method of restoring your files is by trying to bring back your files via data recovery software. Here are some suggestions for preferred data recovery software solutions:
If the first method does not work, we suggest trying to use decryptors for other ransomware viruses, in case your virus is a variant of them. The two primary developers of decryptors are Kaspersky and EmsiSoft, links to which we have provided below:
Urgent! It is strongly advisable to first remove the .java Dharma Virus
threat before attempting any decryption, since it may interfere with
system files and registries. You can do the removal yourself just in 5
minutes, using an advanced malware removal tool.
Method 3: Using Shadow ExplorerTo restore your data in case you have backup set up, it is important to check for shadow copies in Windows using this software if ransomware has not deleted them:
Method 4: Finding .java Dharma Virus decryption key while it communicates it via a network sniffing software.
Another way to decrypt the files is by using a Network Sniffer to get the encryption key, while files are encrypted on your system. A Network Sniffer is a program and/or device monitoring data traveling over a network, such as its internet traffic and internet packets. If you have a sniffer set before the attack happened you might get information about the decryption key. See how-to instructions below:

 STOPZilla Anti Malware
STOPZilla Anti Malware

This article is a good piece of information. Thanks for giving a detailed knowledge about removal of Dharma ransomware and restoration of lost files. Please update information about French101 ransomware
ReplyDeleteNice blog. Thanks for sharing the informative blog on the Dharma ransomware virus. If you are looking for the best Dharma Ransomware Recovery service then you should definitely have a look here. Fast Data Recovery specializes in Ransomware Recovery from DHARMA Ransomware and we have a 100% chance of recovery based on previous DHARMA variant cases.
ReplyDeleteWonderfull blog... Thanks for sharing an informative blog on the data recovery service. If you looking for a data recovery service then you should definitely have a look here. Fast Data Recovery is the largest ransomware recovery service in Australia and New Zeeland with a growing list of international clients.
ReplyDelete